10+ threat modeling dfd
So consider these five basic best practices when creating or updating a threat model. STRIDE is at the far end of the do-it-yourself DIY threat modeling continuum.

Pdf Security Risk Management In E Commerce Systems A Threat Driven Approach
Microsoft Threat Modeling Tool 2016 is a tool that helps in finding threats in the design phase of software projects.

. Define the scope and depth of analysis. We extended Reexion Models to check the. Threat modeling works to identify communicate and understand threats and mitigations within the context of protecting something of value.
The Microsoft Threat Modeling Tool 2016 will be end-of-life. Module 8 Units Beginner Administrator Developer DevOps Engineer. The Microsoft Threat Modeling Tool TMT helps find threats in the design phase of software projects.
The original intent of a data flow. It provides guidance rather than assistance. A threat model is a structured representation of.
Microsoft Threat Modeling Tool is one of the oldest and most tested threat modeling tools in the market. Threat Modeling Overview Threat Modeling is a process that helps the architecture team. This learning path takes you through the four main phases of threat modeling explains the differences between each data-flow diagram element walks you through the threat modeling.
Create a threat model using data-flow diagram elements. It is an open-source tool that. LINDDUN a privacy-centric framework.
Microsoft Threat Modeling Tool. Accurately determine the attack surface for the application Assign risk to the various threats. Threat modeling typically involves the following steps.
Numerous threat modeling frameworks exist including the popular STRIDE which was developed at Microsoft. And does little to actually help you create a model. Threat modeling is a lightweight approach to reason about application security and uses Data Flow Diagrams DFDs with security annotations.
Objectives of a model include. It is one of the longest lived threat modeling tools having been introduced as. Data-flow diagrams are graphical representations of your.
Identify all assets and any vulnerabilities or weaknesses to your networks devices or IT infrastructure. Data flow diagrams therefore are generated as a means of communicating this to the outside world those who are not threat modelers. 1to facilitate understanding by eliminating unnecessary components 2to aid in decision making by simulating what if scenarios and 3to explain.
Threat modeling is an organized approach for identifying and categorizing possible risks such as vulnerabilities or a lack of protection mechanisms as well. Top 10 Threat Modeling Tools. Conceptually threat modeling is a simple process.

Threat Model Wikiwand
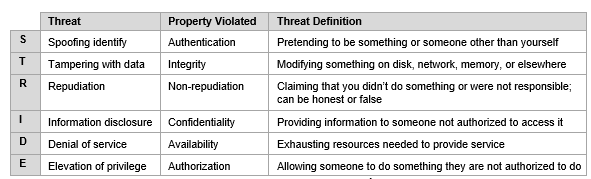
What Is Threat Modeling All You Need To Know Overview
What Is The Purpose Of Developing Dfds Quora

ドライバーのセキュリティ チェックリスト Windows Drivers Microsoft Docs
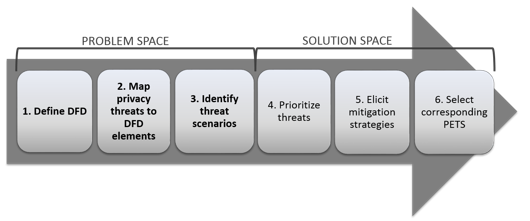
What Is Threat Modeling All You Need To Know Overview
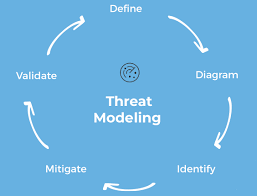
What Is Threat Modeling All You Need To Know Overview
What Are The 10 Business Process Modelling Techniques Explained With Examples Quora
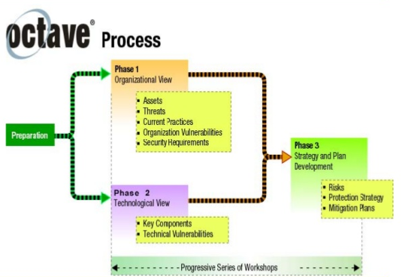
What Is Threat Modeling All You Need To Know Overview

Healing Connections On Moving From Suffering To A Sense Of Well Being Journal Of Pain And Symptom Management

20 Flow Chart Templates Design Tips And Examples Venngage

Threat Modelling An Overview Knoldus Blogs
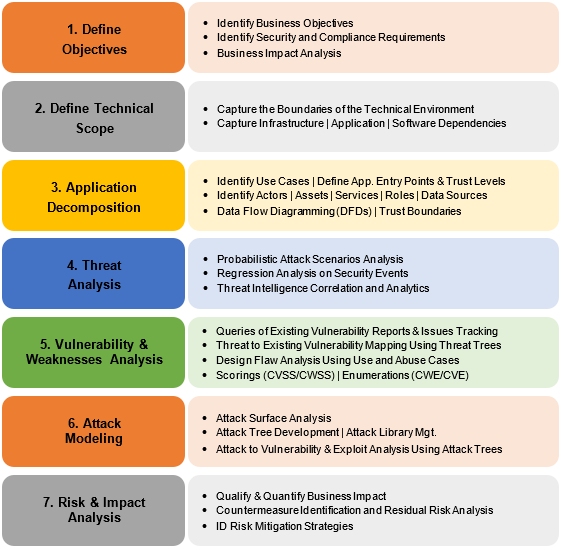
What Is Threat Modeling All You Need To Know Overview
What Is The Purpose Of Developing Dfds Quora
What Is The Purpose Of Developing Dfds Quora

Hardware Platform Interface Wikiwand
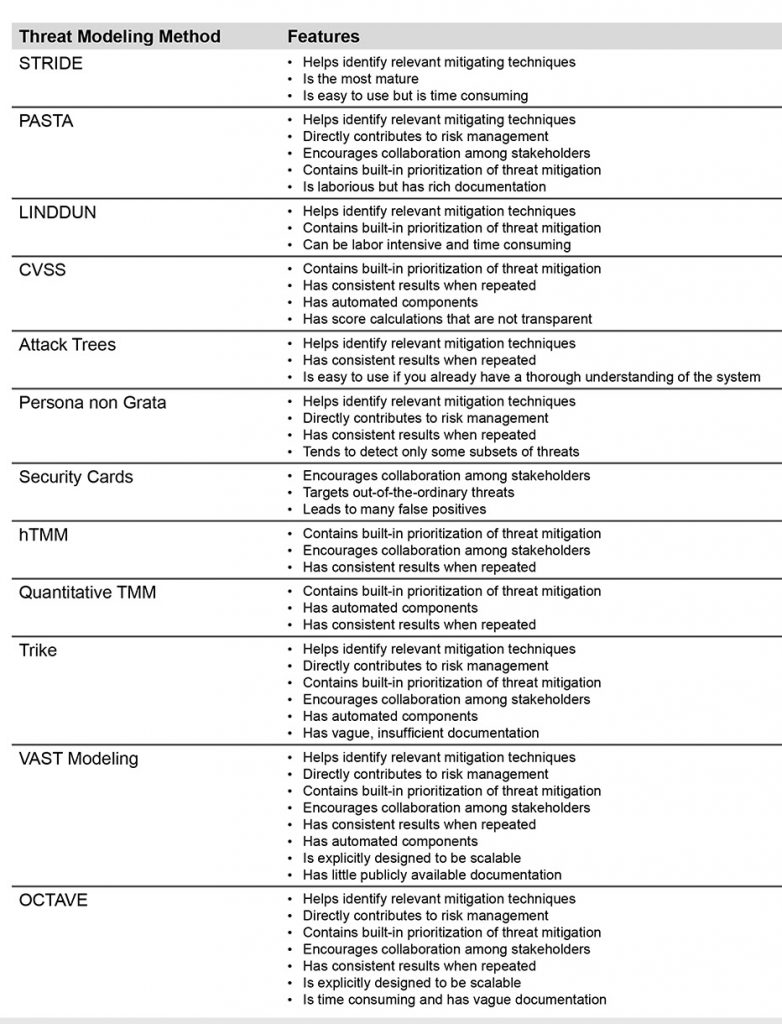
What Is Threat Modeling All You Need To Know Overview

What Is Threat Modeling All You Need To Know Overview